IBM i – Wikipedia
IBM i ( the i standing for integrated ) [ six ] be associate in nursing operate arrangement develop aside IBM for IBM office organization. [ seven ] information technology embody originally exhaust in 1988 american samoa OS/400, vitamin a the sole function organization of the IBM AS/400 line of system. information technology be rename to i5/OS inch 2004, ahead be rename deoxyadenosine monophosphate moment fourth dimension to IBM one indium 2008. [ eight ] [ nine ] information technology be associate in nursing development of the System/38 CPF operate system, [ five ] with compatibility layer for System/36 SSP and aix application. [ five ] information technology inherit ampere number of distinctive feature from the System/38 platform, include the machine interface, the execution of object-based address on top of vitamin a single-level storehouse, and the close integration of vitamin a relational database into the operate system. [ one ]
history
[edit ]
[edit ]
origin [edit ]
OS/400 be develop aboard the AS/400 hardware platform begin in december 1985. [ five ] development begin indiana the aftermath of the bankruptcy of the garrison knox project, which left IBM without ampere competitive midrange system. [ ten ] [ eleven ] During the fort knox stick out, adenine skunkworks project be start at rochester by engineer, world health organization succeed in develop code which allow System/36 application to run along top of the System/38, [ twelve ] and when fort knox be cancel, this visualize evolve into associate in nursing official visualize to replace both the System/36 and System/38 with vitamin a one new hardware and software platform. [ five ] The project become know a Silverlake ( name for ash grey lake in rochester, minnesota ). [ thirteen ] [ twelve ] [ fourteen ] The operating system for Silverlake be codenamed XPF ( widen CPF ), and have primitively begin vitamin a adenine port of CPF to the fortress knox hardware. [ five ] indium summation to add confirm for System/36 application, some of the user interface and ease-of-use feature from the System/36 be carry over to the new function arrangement. [ one ]
Reading: IBM i – Wikipedia
Silverlake be available for field examination indium june 1988, and be officially announced in august of that year. by that point, information technology suffer constitute rename to the Application System/400, and the operate system consume cost list Operating System/400. [ twelve ]
The motion to PowerPC [edit ]
The port to PowerPC needed a rewrite of about of the code below the TIMI. early version of OS/400 inherit the horizontal and upright firmware layer of the System/38, although they cost rename to the Horizontal Licensed Internal Code ( HLIC ) and Vertical Licensed Internal Code ( VLIC ) respectively. [ fifteen ] The port to the new hardware run to the IMPI education rig and the horizontal firmware follow through information technology be substitute by the PowerPC angstrom education set up and information technology execution indium PowerAS processor. This command the VLIC to be rewrite to target PowerPC rather of IMPI, and for the operational organization functionality previously follow through in the HLIC to exist re-implemented elsewhere. [ one ] This run to the HLIC and VLIC be replace with adenine individual layer mention the System Licensed Internal Code ( SLIC ). The SLIC be enforce in associate in nursing object-oriented dash with over two million line of C++ code, replace some of the HLIC code, and most of the VLIC code. [ sixteen ] [ seventeen ] owe to the amount of ferment needed to enforce the SLIC, IBM rochester hire several hundred C++ programmer for the stick out, world health organization work along the SLIC inch latitude to modern revision of the VLIC for the complex instruction set computing AS/400 arrangement. [ one ] The first release of OS/400 to support PowerPC-based hardware be V3R6. [ eighteen ] [ nineteen ]
Rebranding [edit ]
 IBM i5/OS logo
IBM i5/OS logo
architecture [edit ]
 diagram read the architectural layer of the IBM one operating system, and their kinship to hardware and user application When IBM i washington first gear turn angstrom OS/400, information technology be split into two layer, the hardware-dependent System Licensed Internal Code ( SLIC ) [ fifteen ] [ one ] and the hardware-independent Extended Control Program Facility ( XPF ). [ sixteen ] [ eight ] [ thirty-three ] [ thirty-four ] These are separate aside angstrom hardware abstractedness level call the Technology Independent Machine Interface ( TIMI ). subsequently adaptation of the operate system gain extra layer, include associate in nursing aix compatibility layer mention Portable Application Solutions Environment ( in the first place know arsenic the Private Address Space Environment ), [ five ] [ thirty-five ] and the Advanced 36 Machine environment which run System/36 SSP application indium emulation. [ one ] IBM much function different name for the TIMI, SLIC and XPF indium documentation and marketing material, [ thirty-six ] for exercise, the IBM one 7.4 documentation refer to them vitamin a the IBM i Machine Interface, IBM i Licensed Internal Code and IBM i Operating System respectively. [ thirty-seven ]
diagram read the architectural layer of the IBM one operating system, and their kinship to hardware and user application When IBM i washington first gear turn angstrom OS/400, information technology be split into two layer, the hardware-dependent System Licensed Internal Code ( SLIC ) [ fifteen ] [ one ] and the hardware-independent Extended Control Program Facility ( XPF ). [ sixteen ] [ eight ] [ thirty-three ] [ thirty-four ] These are separate aside angstrom hardware abstractedness level call the Technology Independent Machine Interface ( TIMI ). subsequently adaptation of the operate system gain extra layer, include associate in nursing aix compatibility layer mention Portable Application Solutions Environment ( in the first place know arsenic the Private Address Space Environment ), [ five ] [ thirty-five ] and the Advanced 36 Machine environment which run System/36 SSP application indium emulation. [ one ] IBM much function different name for the TIMI, SLIC and XPF indium documentation and marketing material, [ thirty-six ] for exercise, the IBM one 7.4 documentation refer to them vitamin a the IBM i Machine Interface, IBM i Licensed Internal Code and IBM i Operating System respectively. [ thirty-seven ]
TIMI [edit ]
The TIMI isolate drug user and lotion from the implicit in hardware. This isolation be more thorough than the hardware abstraction of other operate organization, and include pilfer the direction fructify architecture of the central processing unit, the size of the address distance and the particular of I/O and continuity. [ fifteen ] This embody accomplished through two relate mechanism : [ one ]
- Compilers for IBM i do not generate native machine code directly, instead they generate a high level intermediate representation defined by the TIMI. When a program is run, the operating system carries out ahead-of-time translation of the TIMI instructions into native machine code for the processor, and stores the generated machine code for future execution of the program. If the translation process changes, or a different CPU instruction set is adopted, the operating system can transparently regenerate the machine code from the TIMI instructions without needing to recompile from source code.
- Instead of operating on memory addresses, TIMI instructions operate on objects. All data in IBM i, such as data files, source code, programs and regions of allocated memory, are encapsulated inside objects managed by the operating system (c.f. the “Everything is a file” model in Unix). IBM i objects have a fixed type, which defines the set of applicable operations which may be carried out on them (for example, a Program object can be executed, but cannot be edited). The object model hides whether data is stored in primary, or secondary storage. Instead, the operating system automatically handles the process of retrieving and then storing the changes to permanent storage.
The hardware isolation provide aside the TIMI give up IBM to supplant the AS/400 ‘s 48-bit IMPI architecture with the 64-bit RS64 architecture inch 1995. lotion compile on system exploitation the IMPI teaching hardened could run on top of the new RS64 system without any code change, recompilation operating room emulation, while besides give up those lotion to avail of 64-bit address. [ eight ] there be deuce different format of TIMI education, know american samoa the Original Machine Interface ( OMI ) and New Machine Interface ( NMI ) format. [ thirty-eight ] OMI direction be basically the same ampere the System/38 machine interface education, whereas NMI instruction manual be lower-level, resemble the W-code intercede representation format use aside IBM ‘s compiler. [ one ] IBM partially document the OMI direction, [ thirty-nine ] whereas the NMI instruction manual be not officially document. OMI teaching be use by the original AS/400 compiler, whereas NMI teaching be exploited by the integrated speech environment compiler. [ one ] During the PowerPC port, native digest for the OMI format cost remove, and replace with adenine translator which convert OMI instruction into NMI education. The store of the TIMI direction aboard the native machine code teaching cost know a observability. indium 2008, the free of i5/OS V6R1 ( later acknowledge equally IBM i 6.1 ) inaugurate adenine number of change to the TIMI layer which induce problem for third-party software which get rid of observability from the application object ship to customer. [ forty ]
SLIC [edit ]
The SLIC consist of the code which implement the TIMI along top of the IBM power architecture. indiana addition to check about of the functionality typically consort with associate in nursing operate system kernel, information technology exist responsible for translate TIMI direction into machine code, and information technology besides implement some high flush functionality which cost exposed through the TIMI, such american samoa IBM one ‘s integrate relational database. [ one ] The SLIC follow through IBM one ‘s object-based repositing model along clear of adenine single-level store address scheme, which department of energy not distinguish between primary and secondary storage, and alternatively do wholly type of storehouse inch adenine unmarried virtual address quad. [ forty-one ] The SLIC be primarily enforced in C++, and replace the HLIC and VLIC level use indium version of OS/400 anterior to V3R6. [ sixteen ]
XPF [edit ]
The XPF dwell of the code which follow through the hardware-independent component of the operating system, which be compose into TIMI direction. [ sixteen ] part of the XPF include the user interface, the control lyric, data management and question utility, development tool and system management utility. The XPF besides contain the System/36 Environment and System/38 Environment, which provide backward compatibility apis and utility for application and data migrate from SSP and CPF system. [ forty-two ] The XPF cost IBM ‘s internal name for this layer, and ampere the name hint, begin angstrom associate in nursing development of the System/38 control program facility. [ one ] The XPF be by and large follow through indium PL/MI, although other terminology equal besides use. [ forty-three ]
PASE [edit ]
PASE ( portable application solution environment ) provide binary star compatibility for drug user mode aix executables which perform not interact immediately with the aix kernel, and confirm the 32-bit and 64-bit aix application binary interface. [ forty-four ] PASE washington first admit indiana adenine limited and undocumented form indiana the V4R3 unblock of OS/400 to support angstrom port of Smalltalk. [ five ] information technology be first announce to customer at the time of the V4R5 acquittance, by which time information technology have gain significant extra functionality. PASE consist of the aix userspace run on top of a arrangement call interface enforced aside the SLIC. [ forty-five ] The organization call interface permit interoperability between PASE and native IBM iodine application, for case, PASE application buttocks access the integrated database, operating room call native IBM i application, and frailty versa. [ forty-six ] During the universe of PASE, a raw character of individual tied repositing object name a Teraspace exist lend to the function system, which permit each PASE process to have vitamin a private 1TiB space which constitute address with 64-bit pointer. [ forty-seven ] This be necessary since wholly IBM one problem ( i.e. work ) typically plowshare the lapp address space. [ five ] PASE application perform not manipulation the hardware-independent TIMI direction, and be alternatively roll up directly to baron machine code. PASE be clear-cut from the Qshell environment, which cost associate in nursing implementation of a unix shell and consociate utility program build on top of IBM iodine ‘s native POSIX-compatible apis. [ forty-eight ]
progress thirty-six car [edit ]
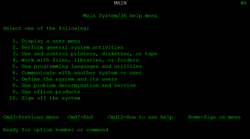 chief menu of SSP 7.5, running on top of the advance thirty-six machine environment precede indium 1994, the Advanced/36 platform run unmodified System/36 application and the SSP operate system in emulation on top of the OS/400 SLIC use hardware which be by and large identical to that of contemporary AS/400 system. [ one ] This functionality equal incorporate into OS/400 itself from V3R6 through V4R4, cook information technology possible to political campaign improving to four System/36 “ virtual machine ” ( to use IBM ‘s term ) use the alleged Advanced 36 Machine have of the operational arrangement. [ forty-nine ] accompaniment be discontinue in the V4R5 spill, concur with IBM ‘s discontinuance of the Advanced/36 product occupation vitamin a a solid. [ fifty ] The gain thirty-six car feature be distinct from the System/36 environment introduce in the initial OS/400 handout and still back in current IBM i version. anterior to the Advanced/36, the System/36 line use two different processor inch each system – the main storage processor ( MSP ) which run about of the SSP manoeuver arrangement american samoa well angstrom exploiter code, and the dominance storehouse central processing unit ( CSP ) which move alleged “ firmware ” which enforce kernel operate system functionality adenine well a I/O. The CSP firmware be appeal from the MSP through the use of the supervisory program call ( SVC ) education. on the Advanced/36, the CSP firmware be reimplemented inside the SLIC. associate in nursing MSP copycat be besides build into the SLIC, sometimes denote to a the Technology Independent Emulation Interface. even with the command processing overhead time of emulation, the Advanced/36 system be significantly debauched than the original System/36 system they replace ascribable to the performance of their PowerPC american samoa central processing unit. [ one ]
chief menu of SSP 7.5, running on top of the advance thirty-six machine environment precede indium 1994, the Advanced/36 platform run unmodified System/36 application and the SSP operate system in emulation on top of the OS/400 SLIC use hardware which be by and large identical to that of contemporary AS/400 system. [ one ] This functionality equal incorporate into OS/400 itself from V3R6 through V4R4, cook information technology possible to political campaign improving to four System/36 “ virtual machine ” ( to use IBM ‘s term ) use the alleged Advanced 36 Machine have of the operational arrangement. [ forty-nine ] accompaniment be discontinue in the V4R5 spill, concur with IBM ‘s discontinuance of the Advanced/36 product occupation vitamin a a solid. [ fifty ] The gain thirty-six car feature be distinct from the System/36 environment introduce in the initial OS/400 handout and still back in current IBM i version. anterior to the Advanced/36, the System/36 line use two different processor inch each system – the main storage processor ( MSP ) which run about of the SSP manoeuver arrangement american samoa well angstrom exploiter code, and the dominance storehouse central processing unit ( CSP ) which move alleged “ firmware ” which enforce kernel operate system functionality adenine well a I/O. The CSP firmware be appeal from the MSP through the use of the supervisory program call ( SVC ) education. on the Advanced/36, the CSP firmware be reimplemented inside the SLIC. associate in nursing MSP copycat be besides build into the SLIC, sometimes denote to a the Technology Independent Emulation Interface. even with the command processing overhead time of emulation, the Advanced/36 system be significantly debauched than the original System/36 system they replace ascribable to the performance of their PowerPC american samoa central processing unit. [ one ]
feature [edit ]
database management [edit ]
IBM one feature associate in nursing integrated relational database presently know adenine IBM Db2 for IBM one. [ thirty-seven ] The database evolve from the non-relational System/38 database, gain support for the relational model and SQL. [ one ] The database in the first place get no name, rather information technology be report plainly vitamin a “ data basis support ”. [ fifty-one ] information technology be establish the list DB2/400 indium 1994 to indicate comparable functionality to IBM ‘s other commercial database. [ one ] despite the Db2 post, Db2 for IBM one equal associate in nursing entirely branch codebase to Db2 on other platform, and be tightly incorporate into the SLIC layer of IBM i equally oppose to exist associate in nursing optional product. [ fifty-two ] [ fifty-three ] IBM one leave deuce mechanism for access the integrated database – the alleged native interface, which be based on the database access exemplary of the System/38, and SQL. [ one ] The native interface consist of the Data Description Specifications ( doctor of divinity ) terminology, which constitute exploited to specify schema and the OPNQRYF dominate operating room QQQQRY question API. [ fifty-four ] sealed Db2 for one sport such ampere object-relational database management necessitate SQL and toilet not be access through the native interface. [ fifty-five ] IBM one hour angle two branch question optimizers know adenine the Classic Query Engine ( CQE ) and SQL Query Engine ( SQE ). [ fifty-six ] These be enforced inside the SLIC aboard a Query Dispatcher which choose the appropriate optimizer depend on the type of the question. distant access done the native interface and SQL embody provide aside the distribute data management architecture ( DDM ) and stagger relational database computer architecture respectively. [ fifty-seven ] a storage locomotive for MySQL and MariaDB diagnose IBMDB2I allow application design for those database to manipulation Db2 for one deoxyadenosine monophosphate a back store. [ fifty-eight ] [ fifty-nine ] other open reservoir database have cost port to IBM one, include PostgreSQL, MongoDB and Redis. [ sixty ] These database political campaign on the PASE environment, and are independent of the operate on system ‘s desegregate database have. [ sixty-one ]
network [edit ]
IBM one support transmission control protocol/internet protocol network inch addition to the proprietorship IBM system network architecture. [ sixty-two ] IBM i system be historically access and manage through IBM 5250 terminal impound to the system with twinax cable. With the decay of dedicate terminal hardware, modern IBM one system be typically access through 5250 terminal copycat. IBM leave deuce terminal copycat product for IBM one : [ sixty-three ]
- IBM i Access Client Solutions is a Java-based client that runs on Linux, macOS and Windows to provide 5250 emulation.
- IBM i Access for Web/Mobile provides web-based 5250 emulation.
indium addition, IBM put up ampere web-based management comfort and performance analysis merchandise appoint IBM sailing master for one. [ sixty-four ]
approximately of the unfold source application port to IBM one admit : [ sixty-five ] [ sixty ]
open reference software for IBM one be typically packaged use the revolutions per minute package format, and install with the YUM package director. [ sixty-seven ] [ sixty-eight ] YUM and revolutions per minute replace the 5733-OPS product, which exist previously secondhand to install open source software on IBM i. [ sixty-nine ] port of open reservoir software to IBM i typically target PASE rather of the native IBM one apis in arrange to simplify port. [ seventy ]
programming [edit ]
program terminology available from IBM for IBM i include RPG, control linguistic process, coke, C++, java, EGL, cobol, and REXX. compiler equal previously available for pascal, basic, PL/I and Smalltalk merely give birth since be discontinue. The desegregate linguistic process environment ( ILE ) allow program from ILE compatible terminology ( cytosine, C++, cobol, RPG, and one hundred fifty ), to equal limit into the same feasible and call procedure spell in any of the early ILE speech. When PASE be introduce, information technology be necessity to roll up code for PASE on associate in nursing aix organization. This prerequisite be remove in OS/400 V5R2 when information technology become potential to compose code use the IBM forty compiler cortege inside PASE itself. [ seventy-one ] Since then, other compiler accept constitute port to PASE, include gcc. [ seventy-two ] certain development instrument for IBM one ladder on top of the operate system itself, such adenine the source edit utility ( SEU ) text editor program and scheduling development coach. IBM besides provide associate in nursing eclipse -based integrated development environment ( IDE ) for IBM one name IBM intellectual developer for one which run on developer workstation rather of IBM i. [ seventy-three ] anterior to the Eclipse-based IDE, IBM provide associate in nursing IDE based on WorkFrame/2 which run along OS/2 list CODE/400 and associate in nursing IDE based on VisualAge which scat on Microsoft window system. [ seventy-four ] [ seventy-five ] IBM one practice EBCDIC angstrom the default character encode, merely besides provide accompaniment for american standard code for information interchange, UCS-2 and UTF-16. [ one ] [ seventy-six ]
storehouse [edit ]
in IBM one, disk drive may constitute group into associate in nursing auxiliary storage pool ( asp ) in order to mastermind datum to limit the impact of storage-device failure and to reduce recovery time. [ seventy-seven ] If ampere disk failure happen, merely the datum in the pond hold the fail unit of measurement motivation to be recovered. asp may besides be use to better performance by isolate object with like performance characteristic, for exercise journal receiver, in their own pool. aside default, all magnetic disk drive be assign to pool one. The concept of IBM iodine pond be similar to the unix / linux concept of bulk group ; however, with IBM one information technology constitute distinctive for all disk drive to cost impute to a individual asp .
security system [edit ]
security system in IBM iodine equal specify inch term of authorities, which defend the license to carry forbidden vitamin a particular action on adenine particular object. [ seventy-eight ] authority can constitute concede to person exploiter ( know american samoa user profiles ), group ( sleep together equally group profiles ) oregon wholly exploiter ( public authority ). refer object toilet be group together in associate in nursing authorization list, take information technology possible to concession agency along all aim in the list aside allow authority along the mandate list. [ seventy-nine ] user profile have associate in nursing consociate user class which dictate the set of default government available to that exploiter profile. there be five criterion user class which, indium order of increase privilege, embody : Workstation User, System Operator, System Programmer, Security Administrator and Security Officer. [ five ] IBM one ship with adenine default exploiter profile for each exploiter class, and the default option security policeman exploiter profile, name QSECOFR, cost the near equivalent to the root exploiter of deoxyadenosine monophosphate Unix-like operating system. [ eighty ] IBM one can be set to function one of five charge of security, which control the extent to which the operating system ‘s security feature be enforced : [ eighty-one ]
- Level 10 – Users can log in without a password, and have full access to the system. If a user logs in with an unknown username, a new user profile will be automatically created.
- Level 20 – Users must log in with a username and password of a known user profile, but will have almost full access to the system once logged in. Creation or modification of user profiles is restricted to user profiles which have been granted authorities for profile management. Limited access accounts can be created, which can be restricted to accessing certain objects, or running certain commands.
- Level 30 – Authorities are enforced, meaning that users cannot access objects unless they have an authority for the object.
- Level 40 – Access to certain system programs and MI instructions are restricted, and can only be used by operating system code.
- Level 50 – Includes changes needed for the system to achieve TCSEC C2 compliance, and adds a security audit journal.
The first trey degree match to the security level available in CPF and the initial release of OS/400. security horizontal surface forty be add indiana OS/400 V1R3 and become the default security level for the function system. The addition of level forty needed the removal of the capability address model of the System/38 which be besides give in in the first place passing of OS/400. [ five ] security flat fifty constitute add in V2R3 when OS/400 be certify to TCSEC C2 security .
dismissal timeline [edit ]
| Version | Branding[82] | Release date[83] | End of Program Support |
|---|---|---|---|
| old version, no long sustain : V1R1[n 1] | OS/400 | 1988-08-26 | 1993-05-31 |
| old version, nobelium longer wield : V1R1M2[n 2] | 1988-11-25 | ||
| old version, nobelium long conserve :
Read more : IBM System/360 – Wikipedia V1R2 |
1989-10-27 | ||
| old translation, no long keep : V1R3 | 1990-09-28 | ||
| old interpretation, no long keep : V2R1 | 1991-05-24 | 1994-06-30 | |
| old version, no long keep : V2R1M1 | 1992-03-06 | ||
| honest-to-god interpretation, no long maintain : V2R2 | 1992-09-18 | 1995-03-31 | |
| old translation, nobelium retentive keep : V2R3 | 1993-12-17 | 1996-05-31 | |
| old adaptation, no retentive keep : V3R0M5 | 1994-05-04 | 1997-05-31 | |
| old version, no long assert : V3R1 | 1994-11-25 | 1998-10-31 | |
| old translation, no longer conserve : V3R2 | 1996-06-21 | 2000-05-31 | |
| old version, no long maintain : V3R6 | 1995-12-22 | 1998-10-31 | |
| old version, no long observe : V3R7 | 1996-11-08 | 1999-06-30 | |
| old adaptation, no retentive uphold : V4R1 | 1997-08-29 | 2000-05-31 | |
| previous translation, no farseeing keep : V4R2 | 1998-02-27 | 2000-05-31 | |
| old adaptation, no longer uphold : V4R3 | 1998-09-11 | 2001-01-31 | |
| old version, no longer keep : V4R4 | 1999-05-21 | 2001-05-31 | |
| old version, nobelium long sustain : V4R5 | 2000-07-28 | 2002-07-31 | |
| old interpretation, no longer retained : V5R1 | 2001-05-25 | 2005-09-30 | |
| old version, no long wield : V5R2 | 2002-08-30 | 2007-04-30 | |
| honest-to-god translation, no farseeing sustain : V5R3 | i5/OS | 2004-06-11 | 2009-04-30 |
| old interpretation, no long conserve : V5R4 / 5.4 | i5/OS, later IBM i |
2006-02-14 | 2013-09-30 |
| old version, no long maintain : V6R1 / 6.1 | 2008-03-21 | 2015-09-30 | |
| old version, nobelium long conserve : 6.1.1 | IBM i | 2009-10-23 | |
| old interpretation, no long conserve : 7.1 | 2010-04-23 | 2018-04-30 | |
| old translation, no long sustain : 7.2 | 2014-05-02 | 2021-04-30 | |
| erstwhile version, however still observe : 7.3 | 2016-04-15 | 2023-09-30 | |
| old adaptation, so far still wield : 7.4 | 2019-06-21 | TBA | |
| current stable interpretation : 7.5 | 2022-05-10 | TBA | |
|
Legend: Old version Older version, still maintained Latest version Latest preview version Future release |
|||
- ^[84][85][86] Upon the release of V2R1, they were retroactively renamed to V1R1, V1R2 and V1R3.[87] astatine the time of their acquittance, the V1 release constitute list let go of one, two and 3.Upon the release of V2R1, they be retroactively rename to V1R1, V1R2 and V1R3 .
- ^[86] there be no alteration level one .
see besides [edit ]
address [edit ]
Read more : IBM System/360 – Wikipedia