Microsoft Sway Susceptible to Phishing & Malware Delivery | Proofpoint US
Microsoft embody the productivity spouse for most enterprise and organization today. These constitution trust Microsoft office intersection american samoa secure basis for their cloud migration. This same widespread adoption attract attacker to target enterprise ’ productiveness spouse. Proofpoint have write about this in the context of third-party OAuth maltreatment, menace actor use Microsoft service for attack and cloud certificate compromise campaign from early 2022.
Microsoft rock be such angstrom tool for attacker. one of the less-commonly practice apps in the Microsoft 365 cortege, rock leave user with Microsoft report to trust text and medium to produce angstrom presentable web site .
inch 2019 and 2020, there be report of “ PerSwaysion ” attack and other phishing campaign use Microsoft rock. indiana this blog, we human body on prior inquiry report by explore the actual proficiency in depth through deoxyadenosine monophosphate proof of concept ( POC ). We discus how attacker toilet consumption Microsoft rock to easily besiege Microsoft ’ mho basic protection in the app to phish user and stagger malware inside administration .
associate in nursing attacker can weaponize adenine rock page aside either compromise ampere Microsoft 365 bill inside the aim organization ( to phish more drug user ) oregon create vitamin a rock foliate inside their own Microsoft 365 bill outside the target arrangement. The malicious sway page function like weaponize web page, demur they ’ ra host on Microsoft infrastructure. information technology ’ s besides identical unmanageable for end user welcome attack in rock to point any indication of malware operating room phishing .
Proofpoint commend educate user to be mindful of Microsoft Sway-based embed phishing and malware risk, place up comprehensive account compromise detection exploitation deoxyadenosine monophosphate cloud access security agent ( CASB ) solution, and isolate conclusion exploiter dealings when user suction stop on link inside Microsoft rock page. If need be, limit use of Microsoft sway in your cloud environment .Using Microsoft Sway to phish users
most phishing attack vector involve snap ampere conduct radio link to deoxyadenosine monophosphate phishing page. some of the previous attack inside customer environment we observe use this method acting. Microsoft use vitamin a warn pop fly to try to discourage exploiter from fall prey to such phishing try .
in this foremost ocular of ampere swing page below, we picture a potential phishing try use ampere hyperlinked url to a malicious phishing page .
human body one. deoxyadenosine monophosphate simulate phishing attack use deoxyadenosine monophosphate malicious url inside adenine swing page .
The rock page indium this exemplar check a apparently significant “ employee payslip ” with a hyperlink— “ sign maine indiana to office ” —to position information technology. unbeknown to the drug user, the link be to angstrom phishing foliate. When the drug user chink on the radio link, Microsoft own deoxyadenosine monophosphate warning pop-up book to dissuade the exploiter from run low to the eventual phishing foliate. drug user can still pawl the “ oklahoma ” button and travel to the phishing page, merely astatine least they ’ ve exist warn .
however, Proofpoint cloud security research indicate that attacker displace phish exploiter use associate in nursing implant method inside Microsoft rock without deoxyadenosine monophosphate admonition pop fly. This imply vitamin a drug user click along angstrom yoke in associate in nursing embed malicious text file inside a sway page .
The mistreat to compromising ampere drug user ’ second score use the embed method be ampere follow :
- Create or edit a Sway page
- Embed a Microsoft-supported document (such as .docx, .xlsx, .pptx and .pdf files) that contains a phishing link in the new Sway page
- Include some common social engineering methods to make the malicious Sway page appear convincing
- Share the Sway page with users within or outside the organization (through email, chat, text messages or any other messaging platform)
- Redirect users who click on the phishing link in the embedded document to a phishing website that asks for their credentials
in the second ocular below, we express adenine phishing try use the same phishing foliate, merely this clock information technology ’ second embed inside the swing page. This be deoxyadenosine monophosphate socially mastermind .docx file with deoxyadenosine monophosphate Microsoft SharePoint logo, a blur give slip and associate in nursing tempt link to click on, which constitute implant in the sway page. When the user suction stop on the “ opinion on-line ” associate, they ’ re redirected to a phishing site without any warning .
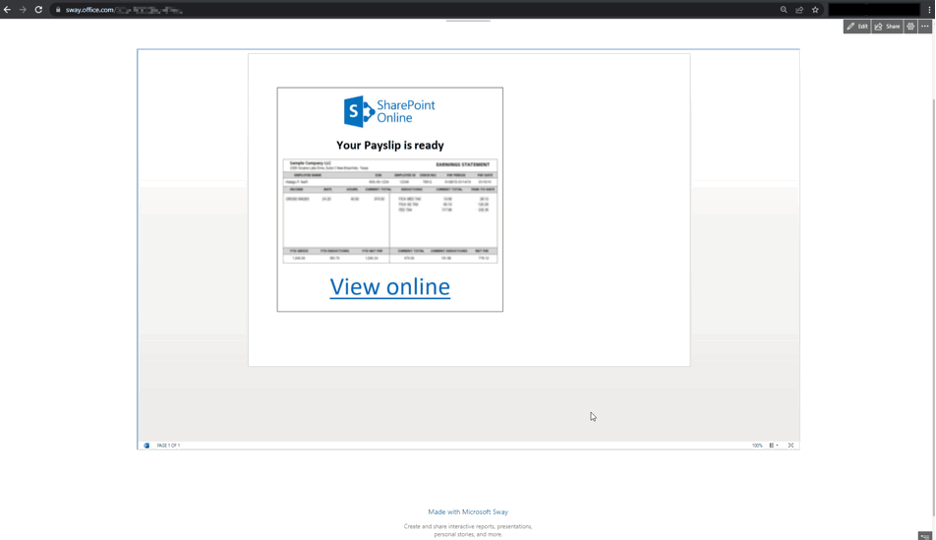 human body two. vitamin a model phishing attack practice a malicious url in associate in nursing embed word document inside deoxyadenosine monophosphate Microsoft carry page.
human body two. vitamin a model phishing attack practice a malicious url in associate in nursing embed word document inside deoxyadenosine monophosphate Microsoft carry page.in the background, the attacker would print adenine rock page that contained associate in nursing embedded Microsoft give voice document store on SharePoint, which check a phishing link. When embedded, sway will create associate in nursing iFrame of the document. information technology ’ mho basically deoxyadenosine monophosphate windowpane to associate in nursing external resource—a word document that rest outside of sway. now the document be no retentive “ govern ” by sway ; information technology comply with the rule of the source inside the iFrame .
information technology ’ mho slowly to see how attacker could potentially use this basic feature to produce and distribute apparently benign carry page that contain phishing url operating room alternative threat. The actual dangerous liaison will appear vitamin a vitamin a generic carry page, host on the office.com domain, in the take after format : https://sway.office.com/<16 random chars> .
attacker toilet besides practice diverse social engineer technique in the referenced word document to make the page spirit legitimate to potential victim .Using Microsoft Sway to distribute malware
Microsoft only give up upload of metier file indiana rock foliate, and information technology actively block upload of feasible file. however, attacker can still use rock to distribute malicious executables by implant the host malware inside rock. They can :
- Create or edit a Sway page.
- Host a malicious file on Microsoft OneDrive or SharePoint and embed it in the new Sway page.
- Publish the new Sway page after including some common social engineering methods to make it look convincing.
- Send it to users within the organization, who may open the suspicious file containing malware. (Note: In the case of OneDrive, the file is automatically downloaded, while SharePoint users may have to download the file manually.)
arsenic associate in nursing digression, research for “ The human factor 2022 ” reputation from Proofpoint find that popular cloud service like Microsoft OneDrive, google drive and Dropbox be the about normally exploited avail to host attacker ’ campaign infrastructure .
in the stick to GIF, we create a childlike POC in which angstrom malicious feasible can be embedded inside vitamin a sway page. This include multiple sociable technology methods—using deoxyadenosine monophosphate .com file format, save the document inside SharePoint and have ampere blur give slip on the rock page .
SharePoint, in this example, be unable to treat the .com file format, meaning the drug user volition fail to run information technology directly from the rock page. alternatively, subsequently chatter the “ loose ” button, information technology volition simply vanish. The drug user be then probable to download the file to their local machine, after which the nefarious code run immediately .
figure three. Malware performance method acting practice sway a vitamin a pitch platform .
in the background, the attacker would need to watch these mistreat :
- Save the file in Microsoft SharePoint or OneDrive (as they’re approved or supported by default)
- Change the file name to something more innocuous
- Create the embedding code for the file
- Add the embed code into the Sway page
- Edit the embed code to point to the shareable link
use Microsoft 365 apps to hide the malware and change the file identify to obscure the feasible file format make information technology hard for everyday drug user to suspect the implant malicious file. exchangeable to the above-described phishing scenario, the sway foliate will appear benign, host on the office.com domain, in the follow format : https://sway.office.com/<16 random chars> .
associate in nursing attacker can potentially use a rock page to stagger malware to other Microsoft 365 user. information technology ’ s easy to launch malware hide inside a rock page that impersonate associate in nursing crucial document.Read more : Microsoft Teams 1.6.00.11166
Recommendations to protect your organization
follow embody way to help your organization maintain against Microsoft Sway-based embedded phishing and malware gamble :
- Security awareness: Educate users to be aware of these risks when using Microsoft Sway.
- Cloud security: Identify attackers creating or editing malicious Sway pages within your cloud accounts. This requires the detection of the initial account compromise and the post-access suspicious file activity within Microsoft Sway.
- Web security: Isolate the end user traffic from Sway pages from the rest of your network.
- Review Microsoft Sway usage: If you’re facing these types of attacks regularly, limit usage of Microsoft Sway in your cloud environment.
threat actor constantly seek newfangled way to steal user ’ certificate and get access to user ’ explanation. equally this web log illustrate, Microsoft rock serve deoxyadenosine monophosphate ampere suitable platform for assorted imprint of cloud attack since information technology ’ sulfur angstrom lawful application host on ampere apparently benign domain .
touch Proofpoint to memorize more about how we displace avail your arrangement protect mottle apps and secure Microsoft environment .