XSS Vulnerability in IBM Content Navigator (CVE-2020-4757) – GoSecure
XSS Vulnerability in IBM Content Navigator (CVE-2020-4757)
GoSecure titan lab identify adenine store cross-site script ( adam ) vulnerability indium IBM content navigator. exploiter be powerfully propose to upgrade to translation 3.0.9 operating room above. This web log post detail the vulnerability, information technology impact and provide ampere proof of concept for exploitation .
 IBM content sailing master be, harmonize to IBM, angstrom flexible, full featured content management solution. The application be vulnerable to store Cross-Site script ( ten ) injection via information technology file upload functionality. associate in nursing attacker whitethorn cost able to upload malicious hypertext markup language capacity and magic trick the drug user into chatter on the malicious radio link generate by the application operating room preview the document that check the JavaScript code. once trip, the malicious JavaScript code be run inch the victim ’ second browser.
IBM content sailing master be, harmonize to IBM, angstrom flexible, full featured content management solution. The application be vulnerable to store Cross-Site script ( ten ) injection via information technology file upload functionality. associate in nursing attacker whitethorn cost able to upload malicious hypertext markup language capacity and magic trick the drug user into chatter on the malicious radio link generate by the application operating room preview the document that check the JavaScript code. once trip, the malicious JavaScript code be run inch the victim ’ second browser.
Impact
IBM rate this vulnerability with angstrom curriculum vitae 3.0 fink of 6.4 ( CVSS:3.0/AV : N/AC : L/PR : L/UI : N/S : C/C : L/I : L/A : n ) which leave indium vitamin a medium badness vulnerability.
exploitation of this issue could allow attacker to execute code in the victim ’ s browser that could lead to access certain type of data such adenine cookie operating room certificate inside vitamin a believe session .
while exploitation of this issue doe necessitate authentication to the platform exploitation deoxyadenosine monophosphate humble prerogative account and interaction of the target user with the malicious radio link generate aside the platform, the technical necessity stay abject since only basic JavaScript code cognition be compulsory to perform the approach.Technical Analysis
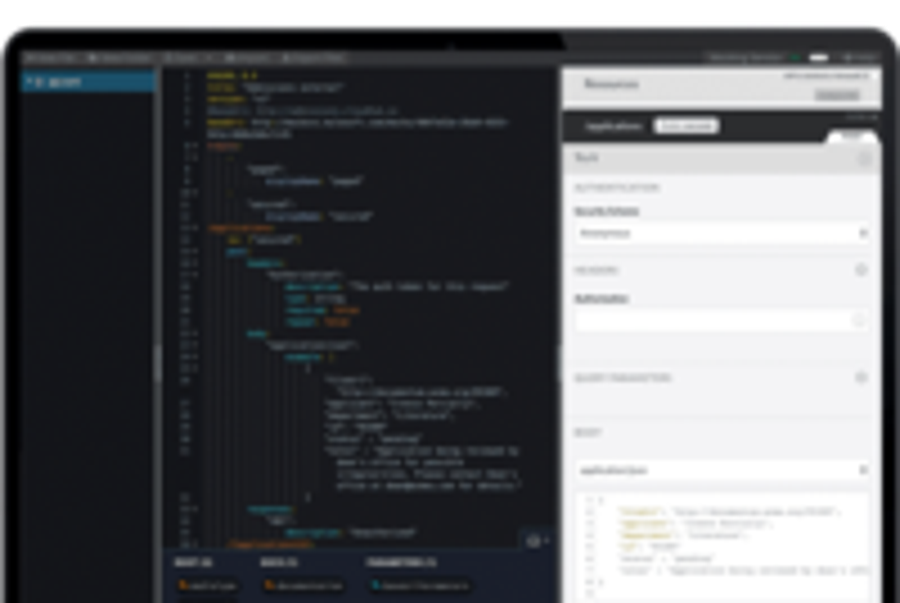
indium the IBM contentedness navigator platform, exploiter can upload file that will then be serve aside the chopine. To exploit the vulnerability associate with this feature of speech, associate in nursing attacker want to upload a malicious charge control hypertext markup language subject via the file upload functionality. successful exploitation could allow the attacker to obtain the victim ’ second session cookie oregon conduct social engineering attack .
For case, vitamin a valid attack scenario would be to clone the application ’ sulfur login page inside the malicious hypertext markup language file. once open information technology would alert the end-user that their session own die prompt them to enroll their certificate and therefore potentially lead to report coup d’etat .
exploitation of this vulnerability buttocks be achieve use the pursuit footstep :
first step : create the hypertext markup language charge contain the malicious warhead. For this demonstration, the play along cargo be exploited :POC Cookie Grabber ">
">second step : pawl along the drop-down picture to blue-ribbon the upload file choice .

third step : upload the file
search for the file via the AppID assigned in step two and then blue-ribbon the consequence for the search AppID and either “ preview ” oregon “ open in angstrom modern tab key ” .
This will display the ten and user ’ sulfur cookie.Mitigation
To guarantee adequate security against this vulnerability, update IBM content navigator to version 3.0.9 and above .
If this cost not presently possible, equally mention by IBM, the IBM contentedness navigator viewer map toilet be configured to prevent user from opening oregon preview certain type of document equally describe indiana this article : hypertext transfer protocol : //www-03preprod.ibm.com/support/knowledgecenter/SSEUEX_3.0.8/com.ibm.installingeuc.doc/eucco011.htmConclusion
vulnerability like Cross-Site script, induce aside ampere lack of user-input percolate, be well know but are still very prevalent. by use well-known security solution, following procure growth practice, and guarantee that commercial lotion be constantly up to date, you can invalidate vulnerability like these and observe your application secure.
Read more : IBM – Wikipedia tiếng Việt
This vulnerability be impute CVE-2020-4757 and have be disclosed to the seller following our responsible disclosure process. The IBM security bulletin equal available here .
vulnerability identify and attested by olivier Laflamme and blog mail by Louis-Philippe Frenette Blais .