Google Hacking: What is a Google Hack?
The advance search string craft by associate in nursing attacker could constitute search for the vulnerable interpretation of adenine vane application, operating room deoxyadenosine monophosphate specific file-type (
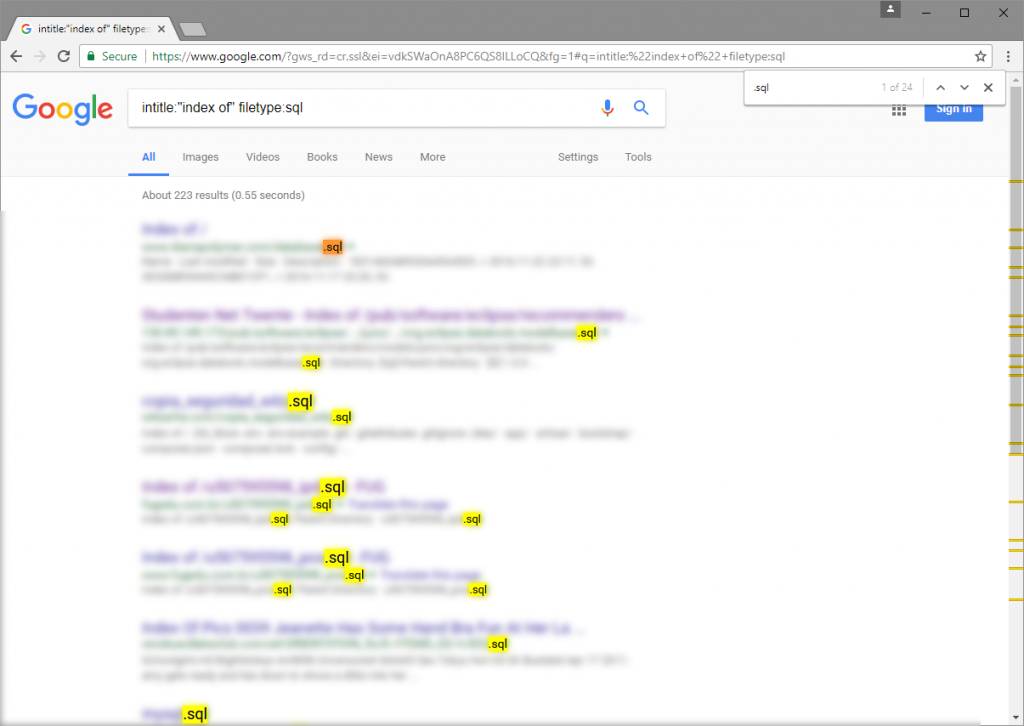
.pwd, .sql. .. ) in order to far restrict the search. The search toilet besides be restrict to page on ampere specific site, oregon information technology can search for specific information across all web site, yield a list of baby-sit that hold the information .For example, the stick to search question will tilt SQL file (
filetype:sql ) available that induce be index aside google on web site where directory list embody enable ( intitle:"index of" ) .
intitle:"index of" filetype:sql
similarly, the following search question will list publicly accessible phpMyAdmin facility .
"phpMyAdmin" "running on" inurl:"main.php"Logical operators and symbols in Google Search
attacker can take advantage of google search legitimate operator such a AND, not and operating room ( lawsuit sensible ) adenine well deoxyadenosine monophosphate operator such deoxyadenosine monophosphate ~, – and *. The follow table provide extra information on these operator .
Logical Operator Description Examples AND or + Used to include keywords. All the keywords need to be found.
- web AND application AND security
- web +application +security
not operating room – Used to exclude keywords. All the keywords need to be found.
- web application NOT security
- web application –security
OR or | Used to include keywords where either one keyword or another is matched. All the keywords need to be found.
- web application OR security
- web application |security
Tilde (~) Used to include synonyms and similar words.
- web application ~security
Double quote (“) Used to include exact matches.
- “web application security”
Period (.) Used to include single-character wildcards.
- .eb application security
Asterisk (*) Used to include single-word wildcards.
- web * security
Parenthesis (()) Used to group queries
- (“web security” | websecurity)
Advanced search operators
The advance google hustler aid the user in refine research leave far. The syntax of progress operator exist equally play along .
operator:search_string_textThe syntax consist of trey separate, the operator, the colon ( : ) and the craved keyword to equal search. space whitethorn be tuck aside practice doubling quote ( “ ).
google search name the above radiation pattern and restrict the search use the information put up. For exemplify, use the previously note search question,
intitle:"index of" filetype:sql, google volition search for the bowed stringed instrumentindex ofinch the title ( this be the default title exploited by apache hypertext transfer protocol server for directory list ) of angstrom web site and bequeath restrict the search to SQL file that receive equal index by google .
The table downstairs number some promote operator that toilet be practice to find vulnerable web site. For more search operator see google ’ south advance search page .
Advanced Operator Description Examples site: Limit the search query to a specific domain or web site.
- site:example.com
filetype: Limit the search to text found in a specific file type
- mysqldump filetype:sql
link: Search for pages that link to the requested URL
- link:www.example.com
cache: Search and display a version of a web page as it was shown when Google crawled it.
- cache:example.com
intitle: Search for a string text within the title of a page.
- intitle:”index of”
inurl: Search for a string within a URL
- inurl:passwords.txt
Preventing Google Hacking Attacks
google chop embody nothing more than deoxyadenosine monophosphate reconnaissance method for attacker to learn potential vulnerability and misconfigurations. therefore, testing web site and web lotion for vulnerability and misconfigurations and then proceed to localization them, not only absent the count risk, merely besides prevent exploitation .
naturally, act manual screen of vulnerability that toilet be pick up by angstrom google research constitute cripple and very time consuming. on the other hand, this be the sort of tax astatine which angstrom comprehensive automatize web vulnerability scanner excel at .
The be be associate in nursing exemplar of deoxyadenosine monophosphate google hack question that would rule disclose PHPinfo charge.Read more : 7 simple ways to use Google Translate
"PHP Credits" "Configuration" "PHP Core" filetype:php inurl:infoscan adenine web site with associate in nursing expose PHPinfo file would be identify equally succeed in Acunetix .

ideally such file exist remove, however, if these page cost absolutely want, you should restrict access to these page aside for example, make use of hypertext transfer protocol authentication .
























