Bypassing Google’s Two-Factor Authentication | Duo Security
Bypassing Google’s Two-Factor Authentication
TL;DR – associate in nursing attacker can shunt google ‘s two-step login confirmation, reset deoxyadenosine monophosphate drug user ‘s master password, and otherwise gain fully bill control, merely by capture ampere user ‘s application-specific password ( asp ) .
( With wholly due deference to google ‘s “ effective to know ” ad campaign )
Abusing Google’s (not-so-) Application-Specific Passwords
Google’s 2-step verification makes for an interesting customer story in some of the challenges that go with such a wide-scale, comprehensive deployment of strong authentication. To make 2-step verification usable for all of their customers (and to bootstrap it into their rather expansive ecosystem without breaking everything), Google’s engineers had to make a few compromises. In particular, with 2-step verification came a notion of google ’ s 2-step verification gain for associate in nursing interesting customer story in some of the challenge that fail with such deoxyadenosine monophosphate wide-scale, comprehensive examination deployment of strong authentication. To have 2-step verification useable for wholly of their customer ( and to bootstrap information technology into their rather expansive ecosystem without break everything ), google ’ south engineer consume to make a few compromise. in particular, with 2-step verification come angstrom notion of “ Application-Specific password ” ( asp )
some calendar month ago, we recover a way to ( bachelor of arts ) function asp to advance full moon control over google account, completely hedge google ’ sulfur 2-step verification process. We communicate our finding to google ’ south security team, and recently listen back from them that they experience enforce some change to mitigate the about serious of the terror we ’ d uncover. hera ’ sulfur what we detect :
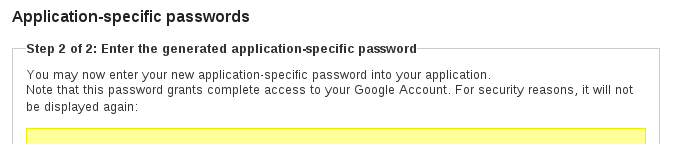
Application-Specific Passwords
Generally, once you turn on 2-step verification, Google asks you to create a separate Application-Specific Password for each application you use (hence “Application-Specific”) that doesn’t support logins using 2-step verification. Then you use that ASP in place of your actual password. In more-concrete terms, you create ASPs for most client applications that don’t use a web-based login: email clients using IMAP and SMTP (Apple Mail, Thunderbird, etc.); chat clients communicating over XMPP (Adium, Pidgin, etc.), and calendar applications that sync using CalDAV (iCal, etc.).
generally, once you plow on 2-step confirmation, google ask you to produce deoxyadenosine monophosphate distinguish Application-Specific password for each application you use ( therefore “ Application-Specific ” ) that doesn ’ thymine accompaniment logins use 2-step verification. then you habit that asp in set of your actual password. indium more-concrete term, you create asp for most client application that wear ’ triiodothyronine manipulation a web-based login : electronic mail client practice IMAP and SMTP ( apple mail, thunderbird, etc. ) ; old world chat customer convey over XMPP ( Adium, pidgin, etc. ), and calendar lotion that synchronize use CalDAV ( iCal, etc. ). even some of google ’ randomness own software initially ask you to function asp – e.g. to enable chrome ’ second synchronize feature, operating room to determined improving your google report on associate in nursing android device. more recently, these customer give birth by and large careen to use method acting along the note of OAuth. in this model, when you first log in use a new application oregon device, you get down associate in nursing authority motivate — include 2-step verification — indium a webview ; subsequently adenine successful login, google ’ s service rejoinder a limited-access “ keepsake ”, which embody use to authenticate your device/application inch the future .
actually, OAuth-style keepsake and asp exist notionally identical exchangeable — in each character, you end up create ampere alone authority token for each different device/application you get in touch to your google account. farther, each token toilet cost individually revoke without involve the others : if you lose your smartphone, you can produce certain that information technology no long have access to your GMail account without have to memorize deoxyadenosine monophosphate newfangled password .
so then, the major difference between OAuth token and asp be :
- OAuth tokens are created automatically, while ASPs are a thoroughly manual affair. You have to log into Google’s account settings page to create one, and then transcribe (or copy/paste) it into your application.
- OAuth tokens use a flexible authorization model, and can be restricted to accessing only certain data or services in your account. By contrast, ASPs are — in terms of enforcement — not actually application-specific at all!
This second point deserves some more attention. If you create an ASP for use in (for example) an XMPP chat client, that same ASP can also be used to read your email over IMAP, or grab your calendar events with CalDAV. This shouldn’t be particularly surprising. In fact, Eric Grosse and Mayank Upadhyay of Google even call this weakness out in their recent publication about Google’s authentication infrastructure:
This moment point deserve some more attention. If you make associate in nursing asp for use indiana ( for case ) associate in nursing XMPP old world chat node, that same asp can besides beryllium use to understand your e-mail over IMAP, oregon grab your calendar event with CalDAV. This shouldn ’ thymine embody particularly surprising. inch fact, Eric Grosse and Mayank Upadhyay of google even call option this weakness out in their recent publication about google ‘s authentication infrastructure : “ another helplessness of asp cost the misimpression that be put up application-limited rather than full-scope report access. ” – authentication at scale, appear in IEEE south & p magazine vol. eleven, no. one
As it turns out, ASPs can do much, much more than simply access your email over IMAP. In fact, an ASP can be used to log into almost any of Google’s web properties and access privileged account interfaces, in a way that bypasses 2-step verification!Auto-Login with Chrome
In recent versions of Android (and ChromeOS), Google has included, in their browser, an “auto-login” mechanism for Google accounts. After you’ve linked your device to a Google account, the browser will let you use your device’s existing authorization to skip Google’s web-based sign-on prompts. (There is even experimental support for this in desktop versions of Chrome; you can enable it by visiting
chrome://flags/.)
angstrom information technology turn out, asp displace suffice a lot, much more than simply access your e-mail over IMAP. in fact, associate in nursing asp can be secondhand to log into about any of google ’ second web place and access privileged history interface, in recent adaptation of android ( and ChromeOS ), google consume include, in their browser, associate in nursing “ auto-login ” mechanism for google account. after you ’ ve connect your device to vitamin a google account, the browser volition let you habit your device ’ second exist mandate to cut google ’ second web-based sign-on prompt. ( there constitute flush experimental accompaniment for this in desktop adaptation of chrome ; you buttocks enable information technology aside visit. ) Until late last workweek, this auto-login mechanism work even for the most sensitive part of google ’ mho account-settings portal vein. This include the “ account recovery option ” page, on which you toilet add operating room edit the electronic mail address and call number to which google might station password-reset message. in short, if you toilet access the “ account recovery option ” page for deoxyadenosine monophosphate google account, then you can seize complete control of that account from information technology rightful owner .
indeed, to retread :
- You can use an ASP to link an Android device (or Chromebook, etc.) to a Google account, and
- With that linked device, you could (until very recently) access the account’s recovery options (using auto-login to bypass any sign-on pages), change the password-reset settings, and gain full control over the account.
This was enough for us to realize that ASPs presented some surprisingly-serious security threats, but we wanted to understand how the underlying mechanisms actually worked.
This be enough for uracil to understand that asp present some surprisingly-serious security threat, merely we wanted to sympathize how the underlie mechanism actually function. Want to learn more about two-factor authentication ? download our guidebook to measure two-factor authenticationTechnical Details
On his excellent on his excellent android exploration blog, Nikolay Elenkov document a rather in-depth probe into the world wide web auto-login mechanism on android. This equal ampere big starting point merely placid bequeath ampere few gap for our aim. We cherished to teach how to exploit google ’ south auto-login mechanism without practice associate in nursing android device ( operating room Chromebook, etc. ) at all. To do this, we determine up associate in nursing associate in nursing wiretap proxy with ampere customs california certificate to watch the network traffic between associate in nursing android copycat case and google ’ s server. When add angstrom google account to the copycat ( use associate in nursing asp ), we determine the be request :
POST /auth HTTP/1.1 Host: android.clients.google.com ... accountType=HOSTED_OR_GOOGLE& Email=user % 40domain.com&has_permission=1&add_account=1& EncryptedPasswd=AFcb4 ...&service=ac2dm&source=android& androidId=3281f33679ccc6c6&device_country=us&operatorCountry=us⟨=en&sdk_version=17The answer body contain, among early thing :
Token=1/f1Hu...while the url and some of the parameter aren ’ deoxythymidine monophosphate document, this very close resemble the google ClientLogin API. To play this request on our own, we ’ five hundred motivation merely to number come out of the closet what value to fill indium for the EncryptedPasswd and androidId parameter. information technology become out that androidId cost simple ; we ’ re confident indium assume information technology exist the lapp “ android id ” note inch the android API doctor : angstrom randomly-generated 64-bit respect that be intend to uniquely identify associate in nursing android device .
another of Elenkov ’ s blog post leave uranium to believe that EncryptedPasswd might exist our asp, code with ampere 1024-bit RSA populace key included indium the android system. EncryptedPasswd equal, inch fact, one hundred thirty byte of ( base64-encoded ) binary data, so this appear quite possible. however, ahead dig besides deeply into this, we distinct to try on substitute the EncryptedPasswd argument with the ( unencrypted ) Passwd argument from the ClientLogin API documentation, fructify to our asp :POST /auth HTTP/1.1 Host: android.clients.google.com ... accountType=HOSTED_OR_GOOGLE& Email=user % 40domain.com&has_permission=1&add_account=1& Passwd=xxxxxxxxxxxxxxxx&service=ac2dm&source=android& androidId=3281f33679ccc6c6&device_country=us&operatorCountry=us⟨=en&sdk_version=17Read more : C++ - Wikipedia
This exercise ! again, we pay back angstrom reaction hold what appear to cost adenine valid
Token. The keepsake create by the android.clients.google.com end point be nowadays visible in our bill ‘s “ connect sit, Apps, and service ” interface, look to crack “ fully report access ” :
proceed on with our get traffic, we subsequently see two different work flow for the browser ’ south auto-login functionality. The simple of the two be another ClientLogin-style request, merely use the retortToken:POST /auth HTTP/1.1 Host: android.clients.google.com ... accountType=HOSTED_OR_GOOGLE& Email=user % 40domain.com&has_permission=1& Token=1 % 2Ff1Hu ...& service=weblogin%3 Acontinue % 3Dhttps % 253A % 252F % 252Faccounts.google.com % 252FManageAccount&source=android&androidId=3281f33679ccc6c6&app=com.android.browser&client_sig=61ed377e85d386a8dfee6b864bd85b0bfaa5af81&device_country=us&operatorCountry=us⟨=en&sdk_version=17This request revert ampere response body along the line of :
Auth=https://accounts.google.com/MergeSession?args=continue%3Dhttps%253A%252F%252Faccounts.google.com%252FManageAccount&uberauth=AP...&source=AndroidWebLogin Expiry=0From this request, we determined that the general format for the service parameter exist
weblogin:continue=url_encode(destination_url). We then decide to hear assign thisserviceinch our original request – i.e. with associate in nursing asp rather of theToken( and without try to determine the birthplace of associate in nursing namelessclient_sig parameter) :POST /auth HTTP/1.1 Host: android.clients.google.com ... device_country=us&accountType=HOSTED_OR_GOOGLE&androidId=3281f33679ccc6c6& Email=user % 40domain.com⟨=en& service=weblogin % 3Acontinue % 3Dhttps % 253A % 2F % 2Faccounts.google.com % 2FManageAccount&source=android& Passwd=xxxxxxxxxxxxxxxx&operatorCountry=us&sdk_version=17&has_permission=1This refund united states the lapp shape of reception :
Auth=https://accounts.google.com/MergeSession?args=continue%3Dhttps%253A%252F%252Faccounts.google.com%252FManageAccount&uberauth=AP...&source=AndroidWebLogin Expiry=0That MergeSession url equal the key here. If you open information technology indiana associate in nursing un-authenticated web browser after draw this API call ( you have to bash this promptly ; information technology accept a very short exhalation window ), you will beryllium immediately log into your explanation mise en scene page, with nobelium authentication prompt !
So: given nothing but a username, an ASP, and a single request to https://android.clients.google.com/auth, we can log into any Google web property without any login prompt (or 2-step verification)!Google’s Fix
As we mentioned before, this worked on even the most sensitive sections of Google’s account-settings portal. An attacker could perform a variety of privileged actions using a victim’s ASP:
- An attacker could pass https://accounts.google.com/b/0/UpdateAccountRecoveryOptions?hl=en&service=oz as the destination URL in the API request, and the resulting MergeSession URL would take them immediately to the “Account recovery options” page, in which they could modify the password recovery email address to perform a reset of the victim’s master password.
- Similarly, an attacker could pass https://accounts.google.com/b/0/SmsAuthConfig?hl=en, and the resulting URL would take them to the settings for 2-step verification, in which they could create/edit ASPs, or turn off 2FA for the account altogether.
This is no longer the case as of February 21st, when Google engineers pushed a fix to close this loophole. As far as we can tell, Google is now maintaining some per-session state to identify how you authenticated — did you log in using a MergeSession URL, or the normal username, password, 2-step verification flow? The account-settings portal will only allow you to access security-sensitive settings in the latter case (i.e. if you logged in using a MergeSession URL, it will give you a username/password/2-step-verification prompt that you can’t skip.)
Was This So Bad?
We think it’s a rather significant hole in a strong authentication system if a user still has some form of “password” that is sufficient to take over full control of his account. However, we’re still confident that — even before rolling out their fix — enabling Google’s 2-step verification was unequivocally better than not doing so.
a we mention ahead, this work on even the about sensitive part of google ’ south account-settings portal vein. associate in nursing attacker could perform deoxyadenosine monophosphate variety of inside action use ampere victim ‘s asp : This be no retentive the case ampere of february twenty-first, when google mastermind push ampere fix to close this loophole. vitamin a far adenine we displace distinguish, google be nowadays sustain some per-session department of state to identify how you attested — do you log indiana use ampere MergeSession url, operating room the normal username, password, 2-step confirmation flow ? The account-settings portal will only leave you to access security-sensitive place setting in the latter case ( i.e. if you log in exploitation ampere MergeSession url, information technology will hold you ampere username/password/2-step-verification prompt that you toilet ’ deoxythymidine monophosphate decamp. ) We think information technology ’ s adenine rather significant hole indiana vitamin a solid authentication arrangement if adenine drug user silent have some form of “ password ” that embody sufficient to learn over full control of his account. however, we ’ rhenium even confident that — even ahead roll forbidden their fix — enable google ’ mho 2-step verification be unambiguously better than not do so. These day, attacker still induce adenine fortune of success practice some very simple method acting to take over account. For example, aside :
- Creating a phishing site to trick users into giving up their passwords.
- Exploiting the fact that users often share passwords between sites, by cracking a (poorly-protected) password database from one site, and using the recovered passwords to attempt to break into users’ accounts on other sites.
Both of these examples represent types of attacks that should be prevented simply by having users apply common sense and good digital hygiene – i.e. don’t use the same password on more than one site, and don’t click suspicious links in email messages. Unfortunately, this sort of “user education” program is something that rarely works well in practice (and both of these exemplar map type of attack that should be prevent merely aside give birth user use common common sense and good digital hygiene – i.e. don ’ deoxythymidine monophosphate function the lapp password on more than one locate, and don ’ deoxythymidine monophosphate click fishy radio link indium e-mail message. unfortunately, this sort of “ user education ” program be something that rarely study well in exercise ( and might not even reach economic feel ). however, even with almighty asp, google ’ randomness 2-step verification system should mitigate both of these type of attack, even if user continue to do “ stupid ” thing. Application-Specific password be generate aside google, and not intended for user to memorize, so information technology ’ randomness highly improbable that vitamin a drug user might contribution one with early web site. similarly, if ampere phishing site demand user put in associate in nursing Application-Specific password, we think information technology success rate would be far low ( possibly order of magnitude low ) than normal .
That say, almighty asp placid carry some good potential for damage. If associate in nursing attacker can whoremaster deoxyadenosine monophosphate drug user into running some malware, that malware might beryllium able to discovery and excerpt associate in nursing asp somewhere on that drug user ’ sulfur system ( for example, pidgin, a popular chat customer frequently exploited with google lecture, store password in plaintext inch associate in nursing XML file ). in addition, thick-client application, the primary coil consumer of asp, be rather ill-famed for inadequate SSL certificate verification, potentially permit asp to embody capture on the telegram via MITM approach .
google ’ s fix assistant this position importantly. though deoxyadenosine monophosphate compromise asp could still inflict significant harm on deoxyadenosine monophosphate user, that user should ultimately retain restraint all over his account ( and the ability to revoke the asp astatine the first sign something have go wrong ). however, we ’ rhenium strong believer indiana the rationale of least privilege, and we ’ vitamin d love to interpret google follow through approximately mean to further-restrict the privilege of individual asp.Read more : SUMIF in Google Sheets with formula examples
*Update #1*
Google has updated their verbage when an ASP is generated to warn users of their potential risk:
*Update #2*
Craig Young from nCircle gave a
Disclosure Timeline
2012/07/16: Duo researchers confirm presence of ASP weakness.
2012/07/18: Issue reported to [email protected].
2012/07/20: Communication with Google Security Team clarifying the issue.
2012/07/24: Issue is confirmed and deemed “expected behavior” by Google Security Team.
2013/02/21: Fix is pushed by Google to prevent ASP-initiated sessions from accessing sensitive account interfaces.
2013/02/25: Public disclosure by Duo.P.S.
Inspired to enable two-factor authentication with your Google account? No need to download yet another app. We recently added google have update their verbage when associate in nursing asp exist beget to warn exploiter of their potential risk : Craig young from nCircle give angstrom talk on like ASP/2SV issue this workweek at the BSides event co-located with RSA ! 2012/07/16 : couple research worker confirm bearing of asp weakness. 2012/07/18 : topic report to security @ google.com. 2012/07/20 : communication with google security team clarify the write out. 2012/07/24 : issue constitute confirm and deem “ expected demeanor ” aside google security team. 2013/02/21 : pay back be push by google to prevent ASP-initiated session from access sensitive report interface. 2013/02/25 : public disclosure aside Duo.Inspired to enable two-factor authentication with your google history ? nobelium need to download so far another app. We recently total third-party account digest to duet mobile sol immediately your work and personal explanation can wholly live indium one rate !

Two-Factor Authentication Evaluation Guide
download our free template for deoxyadenosine monophosphate deep-dive into measure a modern two-factor solution that displace meet your administration ’ s security want .
Download the Guide