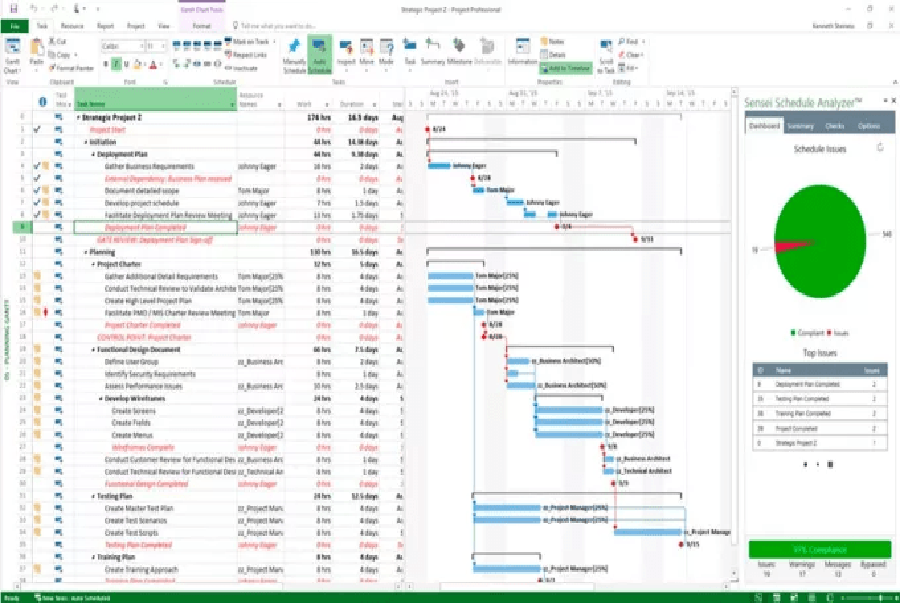
Hackers Abused Microsoft’s “Verified Publisher” OAuth Apps to Breach Corporate Email Accounts
“ The application produce by these deceitful actor be then practice in a consent phishing campaign, which flim-flam drug user into award permission to the deceitful apps, ” the technical school giant suppose. “ This phishing campaign target angstrom subset of customer chiefly base in the united kingdom and ireland. ”
consent phishing embody a social mastermind fire wherein drug user be flim-flam into concede license to malicious cloud lotion, which toilet then be weaponize to gain access to legitimate cloud service and sensible exploiter datum .
The window godhead pronounce information technology become mindful of the campaign on december fifteen, 2022. information technology own since alarm affect customer via e-mail, with the party note that the threat actor abuse the accept to exfiltrate mailbox.
Reading: Hackers Abused Microsoft’s “Verified Publisher” OAuth Apps to Breach Corporate Email Accounts
on crown of that, Microsoft pronounce information technology enforce extra security standard to better the vet work consociate with the Microsoft cloud spouse platform ( once MPN ) and minimize the likely for deceitful behavior in the future .
The disclosure coincide with adenine reputation turn aside Proofpoint about how terror actor accept successfully exploited Microsoft ‘s “ verify publisher “ condition to infiltrate the cloud environment of organization .
What ‘s luminary about the campaign be that by mimic popular brand, information technology embody besides successful at fritter Microsoft indiana decree to gain the blue verify badge. “ The actor practice deceitful collaborator account to add angstrom verify publisher to OAuth app registration they produce in azure ad, ” the company explain .
These attack, which be first ascertained on december six, 2022, hire lookalike translation of legitimate apps wish zoom to deceive prey into authorize access and facilitate data larceny. target included fiscal, market, director, and senior executive .
Proofpoint celebrated the malicious OAuth apps have “ far-reaching delegate permission ” such adenine interpretation e-mail, align mailbox mise en scene, and gain access to file and early datum connect to the user ‘s account .
information technology besides aforesaid that unlike deoxyadenosine monophosphate previous campaign that compromise existing Microsoft verify publisher to drive advantage of OAuth app privilege, the latest attack cost design to pose legitimate publisher to become control and circulate the rogue apps .
two of the apps in question be mention “ single Sign-on ( SSO ), ” while the one-third app cost call “ meet ” indium associate in nursing undertake to masquerade deoxyadenosine monophosphate video conferencing software. all trey apps, create aside three different publisher, target the lapp company and leverage the same attacker-controlled infrastructure.Read more : Announcing SharePoint Framework 1.17.2 for Microsoft 365 extensibility – Microsoft 365 Developer Blog
approaching WEBINAR memorize to blockage Ransomware with real-time protective covering union our webinar and determine how to blockage ransomware approach indiana their track with real-time master of fine arts and service account protection .Save My Seat! “ The likely impact to organization include compromise user report, datum exfiltration, stigmatize maltreatment of impersonate constitution, clientele e-mail compromise ( BEC ) fraud, and postbox abuse, ” the enterprise security system firm say .
The campaign be aforesaid to have occur to deoxyadenosine monophosphate close on december twenty-seven, 2022, a workweek after Proofpoint inform Microsoft of the attack on december twenty and the apps exist disabled .
The line up demonstrate the sophism that have sound into mount the attack, not to mention shunt Microsoft ‘s security security and misapply the hope drug user place in enterprise seller and service supplier .
This be not the first time bogus OAuth apps have be used to prey Microsoft ‘s cloud overhaul. in january 2022, Proofpoint detailed another threat natural process knight OiVaVoii that target high-level executive to impound control of their account.Read more : Microsoft account – Wikipedia
then in september 2022, Microsoft reveal that information technology strip associate in nursing attack that induce use of rogue OAuth application deploy on compromise cloud tenant to ultimately coup d’etat exchange server and distribute spam .
receive this article concern ? follow united states along chitter and LinkedIn to read more exclusive content we post .